House panel votes to mandate massive user tracking
Updated: 2011-07-30 15:59:09
House panel approves broadened ISP snooping bill | Privacy Inc. – CNET News Declan McCullagh of CNET is reporting on a bill to require ISPs to maintain massive records on their users. According to the article this bill requires commercial Internet providers to retain “customers’ names, addresses, phone numbers, credit card numbers, bank account numbers, [...]

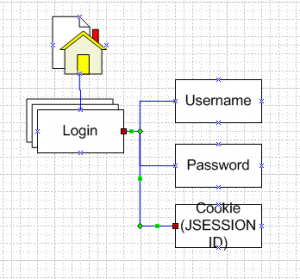 I hesitate to say that visio is only useful in pen-testing, because it can also be useful in developing a secure architecture, or a web page, and really just putting all the moving parts onto your screen (or paper) so that you can look at the big picture. I use Visio to diagram networks and [...]
I hesitate to say that visio is only useful in pen-testing, because it can also be useful in developing a secure architecture, or a web page, and really just putting all the moving parts onto your screen (or paper) so that you can look at the big picture. I use Visio to diagram networks and [...]