Forbes picks up the Tech Review article.
Updated: 2011-06-29 19:06:12
How Visiting Competitors’ Websites May Give Away Your Business Secrets – Kashmir Hill – The Not-So Private Parts – Forbes: “” Odd that they describe a 15 year old company as a “startup”….

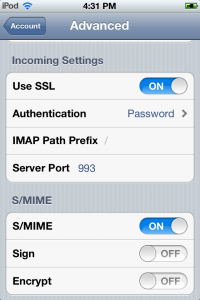 My last post on the topic of S/MIME on iOS 5 got a lot of helpful comments from readers filled in the gaps left by Apple’s current lack of documentation on this topic. The previous article is still the best place for information on how to set up your device to use S/MIME. This post [...]
My last post on the topic of S/MIME on iOS 5 got a lot of helpful comments from readers filled in the gaps left by Apple’s current lack of documentation on this topic. The previous article is still the best place for information on how to set up your device to use S/MIME. This post [...]