Question from a long time customer
Updated: 2009-09-27 21:10:29
A long time customer recently sent in the following question. Since it should be of broad interest, I asked his permission to anonymous post and answer it here.
How do you know that subscribing to an anonymizer does not simply mark you for observation?
We all know the NSA is capable of intercepting any electronic communication, and [...]

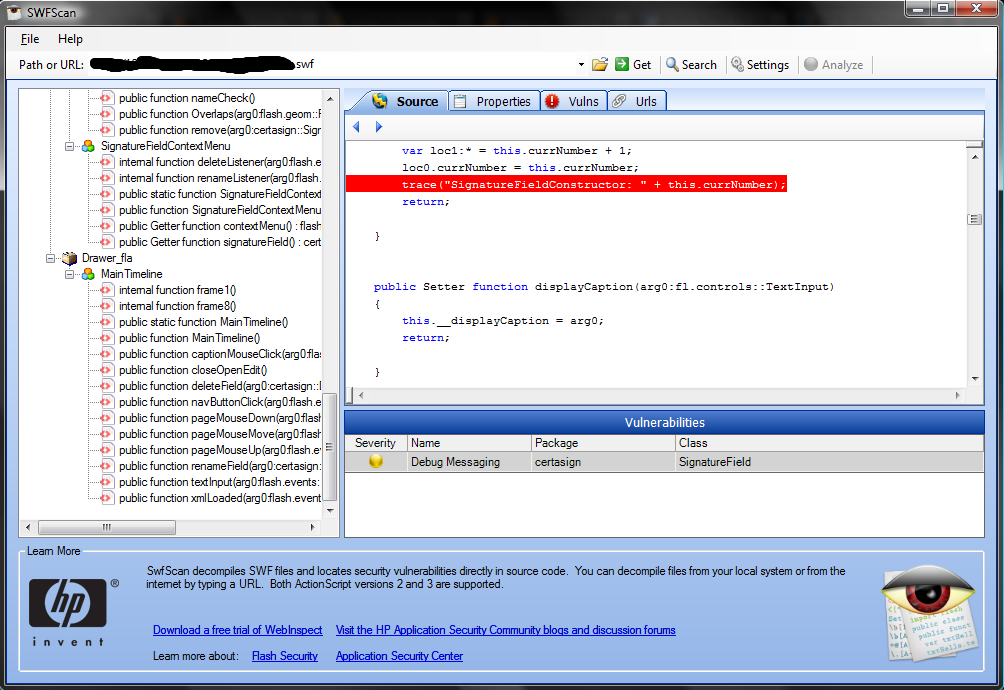 One of the most expanded targets lately in vulnerability research is Adobe’s Flash. It has become a common everyday occurrence on the web; everything from banners, to games, to file uploads. It’s almost hard to find a mainstream site that doesn’t have some sort of flash application running somewhere within the domain. As a result [...]
One of the most expanded targets lately in vulnerability research is Adobe’s Flash. It has become a common everyday occurrence on the web; everything from banners, to games, to file uploads. It’s almost hard to find a mainstream site that doesn’t have some sort of flash application running somewhere within the domain. As a result [...]